Virtual Desktop Infrastructure with a twist
Although the process of moving into a dispersed working environment started some years ago with BYOD, CYOD, DaaS offerings from many software houses and cloud providers the current Covid-19 situation forced many organizations of all sizes to find efficient and swift solutions for remote workers.
The current landscape is not simple as there are many competing offerings and non-IT companies might get discouraged or even mislead by strong marketing into selecting a solution which in their particular case might not be the most appropriate one.
As an IT optimization company, we always try implementing for our customers the solution which offers the right balance features vs costs and the current post (and maybe others) will highlight several options of technologies that might reduce drastically the TCO.
The main reasons for getting a VDIs:
- Ubiquitous secure access over HTTPs to a secure, controlled and compliant VDI
- Granular access to legacy applications which are usually available only in companies intranets
- Granular access to file shares and intranet only web sites.
- Enhanced mobility for user data: user data is available form any device and selectively synced across devices.
- Security & compliancy (antivirus/antimalware policies, SIEM, backup, data leakage protection, encryption)
The VDIs can be categorized based on their delivery:
1. Hosted Shared Desktop
Sometimes referred to as session virtualization. Usually delivered via terminal services (Remote Desktop Services). The users get a session on a Windows Server and have his/her own profile data stored via user profile disks. FSLogix profiles, Citrix user profile disks.
2. VDIs dedicated
The virtual desktops are in fact virtual machines hosted on a hypervisor like (Vmware ESXi, MS Hyper-V, XenServer), or in the public clouds (Azure, AWS, GCS). The dedicated term refers to the fact that there is a clear assignment user to VDI and grants enhanced capabilities for the owner (administrative access, specific applications, policies, etc)
3. VDIs pooled
Like above these are virtual machines but they are pooled meaning that each time a user connects to a pooled VDI it gets a random VDI from a set and his/her profiles are mounted so it gives the illusion of a "personal" VDI.
4. Kiosk VDIs
Pooled VDIs with no persistence for user data. After log off, all the changes are reverted back to the initial image.
Various technologies can be mixed to deliver the 4 types of VDIs. Traditionally MS RS/RDS and Citrix were the main providers but lately, additional players emerged. With the introduction of public clouds and the capabilities of interconnecting on-premises infrastructure with public cloud islands the number of components and IT architecture complexity increased. It won't be realistic covering all possible architectural options so I would mention just a few "twists" to traditional designs.
Use TeamViewer to remotely access on-premise dedicated VDIs.
Organizations having virtualization capabilities Vmware ESXi, Microsoft Hyper-V, XenServer, and enough capacity can create virtual desktops as per company standards. Being located inside the intranet the VDIs will have seamless access to internal applications and files.
Teamviewer offers solutions to remote connectivity, solutions based on proxy tunneling https sessions. A client app deployed on VDIs will establish a secure tunnel towards the TeamViewer cloud servers.
The end-users access via a client app or browser the provider clouds (TeamViewer) and after authentication (MFA possible) the session are hand-shaken and proxied allowing seamless access to the on-premises VDI. As the virtual desktop capacity is delivered from an on-premise datacenter you can optimize the footprint (storage deduplication, thin provisioning, oversubscription for CPU/RAM based on usage patterns, etc). Always the prices for computing power should be much better compared with cloud-based counterparts (AWS, Azure, GCP).
About prices
List prices will vary between 4 EUR per month/per user for individual access to 6 EUR/month/user (for additional features meetings, reporting). The market is very dynamic so don't be lured in the first article claiming that it has superior costs to the other. Ask for a trial, negotiate the contract, or have an MSP like Expertware negotiating the best solution for you.
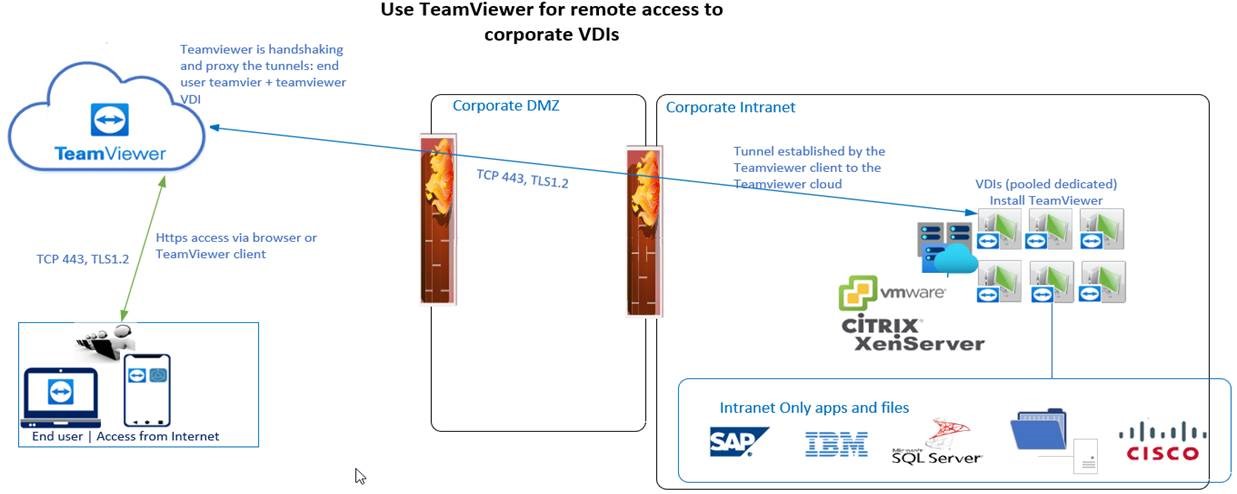
Team viewer can be accessed from the end-user PC and control the sharing capability (disabling file sharing).
Besides providing access to the virtual machines / physical desktops team viewer offers additional meetings and remote support capabilities.
For a full list of features check here.
Use Awingu / Parallels /Splashtop as gateway to on premises VDIs
A different approach has been taken by Awingu (Belgian company), Parallels (known for the iOS products), and more recently Splashtop (US-based). These companies offer a software gateway / remote access server which presents connections to internal desktops, servers, and applications via a browser web portal (HTML5 for some).
The network protocols like RDP (Remote Desktop), CIFS (Common Internet File System) are tunneled by the Gateway in HTTPS / TLS1.2 sessions (check Awingu architecture). They offer simpler management and alternative for an RDS farm deployment.
Parallels positions themselves more as an enhancer for the existing RDS farms so for companies not having an RDS deployment Awingu and Splashtop might be better positioned.
Comparison of Awingu / Splashtop
| License type | Price (per month, per user) | Details | |
| Awingu | Concurrent user | 7 eur | Minimum order: 20 users paid yearly |
| Splashtop | Named user | 4.58 eur | Splashtop Business Access, paid yearly |
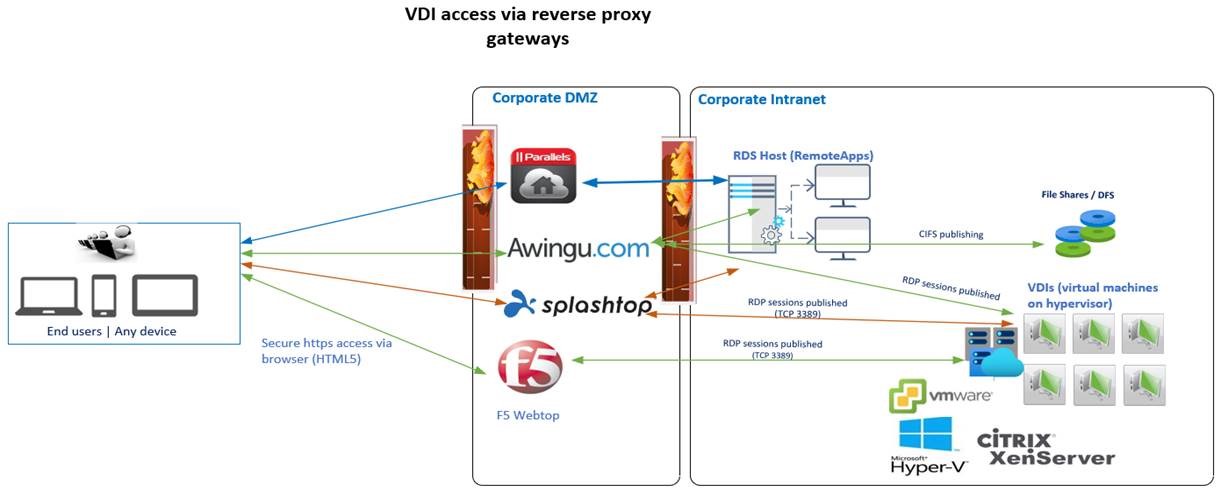
For companies using F5 load balancers with the APM module, there is the option (no additional costs) to configure Remote Desktop Access towards the provisioned VDIs. The management is more cumbersome as for each user a filter directing it to his/her VDI is required.
Leverage existing On-prem RDS farm with HTML5 Web client enabling cloud burst
During the Covid-19 pandemic, we had to apply a hybrid architecture for customers having already RDS farms and on-premises hypervisor clusters but not being able to scale for the number of users they had to provision. The approach was to configure a site to site VPN between on-premises data center(s) and a tenant in public clouds like Azure or AWS and provision additional VDIs (Win 10 or Win 10 Multi-Session) in the cloud. Although there is a longer path establishing the RDS sessions to the cloud VDIs the solution proved performant and it saved costs compared to Windows Virtual Desktops DaaS offering from Microsoft.
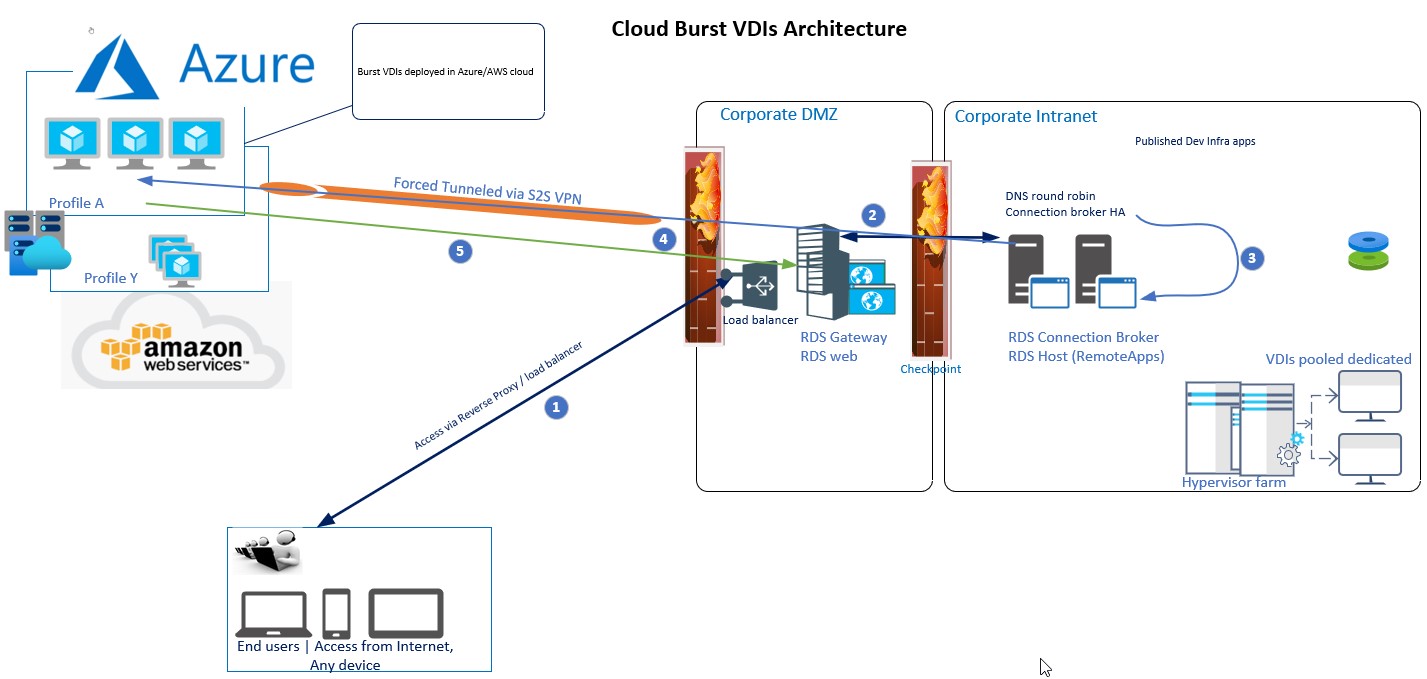
For security and compliance reasons all network traffic from the cloud VDIs are routed via the Internal infrastructure where it is monitored (IDS/SIEM). The configuration for a site to site VPN with forced tunneling is described here. It will require the proper planning of resource groups, VMnets, Virtual Network Gateway, NSGs, routes, etc in Azure and configuration on the on-premise firewall (access rules/routing / NAT).
From RDS 2016 onwards, Microsoft released an HTML5 web client. The result is a smoother HTML5 only access to the on VDIs and Apps compared to the traditional /rdweb web. The HTML5 web client can be configured via Powershell and it is reachable via https://your-RDS-farm-FQDN/webclient.
There are still many combinations possible, using small RDS farms in intranet and publishing via Azure AD Application Proxy, using WVS, using Citrix cloud, GoToMyPC, LogMeIn, Linux KVM, Screens … but we will leave those scenarios for a future post.
We hope you'll find these VDI architectural "twists" useful and we are looking forward to your suggestions for solutions which we should describe or validate. Depending on your IT landscape these suggestions might prove useful.
If you would like to hand over the analysis, implementation, and the operational management to a trusted service provider please contact us @ Expertware.net.
We are always aiming to provide innovative solutions optimizing the IT and business processes landscape for our customers.

Copyright © 2020 - All Right Reserved.